Ransomware Resolution in 24 Hours
Ransomware in your systems? We have the technology and expertise to eliminate the threat and restore business operations. Contact us to secure your business!
Don’t let ransomware destroy your business. At DARKDATA, we restore your systems and data quickly and efficiently.
Call now and get back to normal operations in hours!
- 4,7 (93 reviews)
Ransomware attacks solved
success rate
years of experience

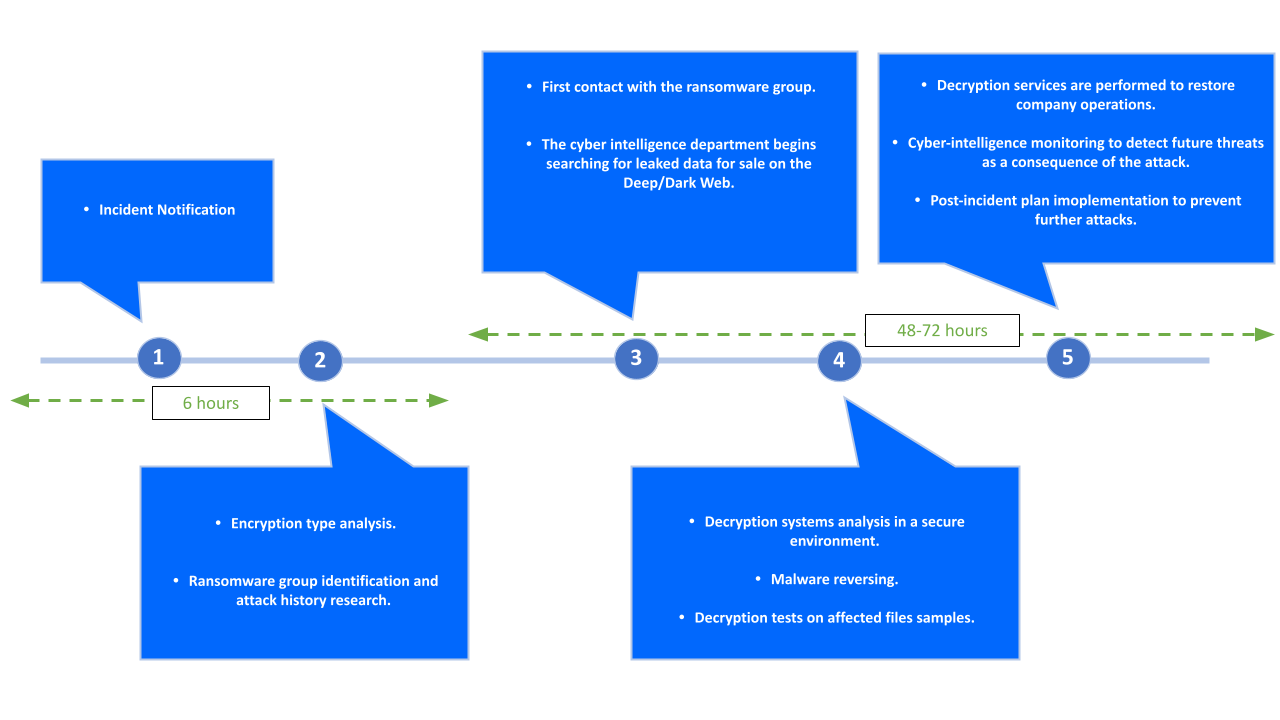
Time is a Key Success Factor in Resolution
Early notification of a ransomware attack is crucial for a positive outcome. It is very important to avoid any contact with the attacking group until DarkData specialists take control.
Testimonials
Success Stories
«The incident response team was extremely efficient and professional. They restored our systems in less than 24 hours and helped us implement better security practices to prevent future incidents.»

Technology Company
«Thanks to their quick intervention, we were able to recover our critical data without paying the ransom. Their knowledge and expertise in handling ransomware gave us great peace of mind during a crisis.»

Hospital
«The immediate response and continuous support were exceptional. They not only managed to decrypt all the files but also recovered our clients’ data that the attackers had put up for sale.»

Law Firm
«The team’s personalized attention and proactive approach allowed us to resume operations with minimal interruptions. We appreciated their patience and clarity throughout the entire process.»

Small Business
Ransomware Timeline: Response Times
Ransomware Characteristics
There are currently hundreds of different ransomware malware families. Additionally, some older families are reactivated through code modifications by various criminal groups. Ransomware exists for Microsoft, GNU/Linux, and MAC OS X operating systems, as well as for mobile devices.
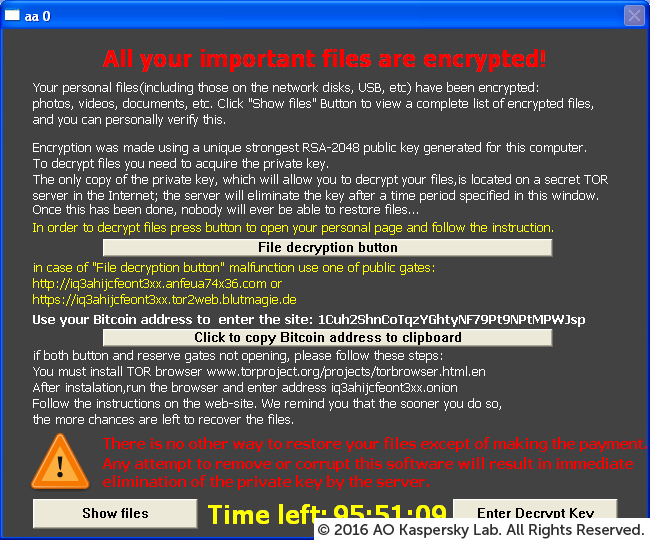
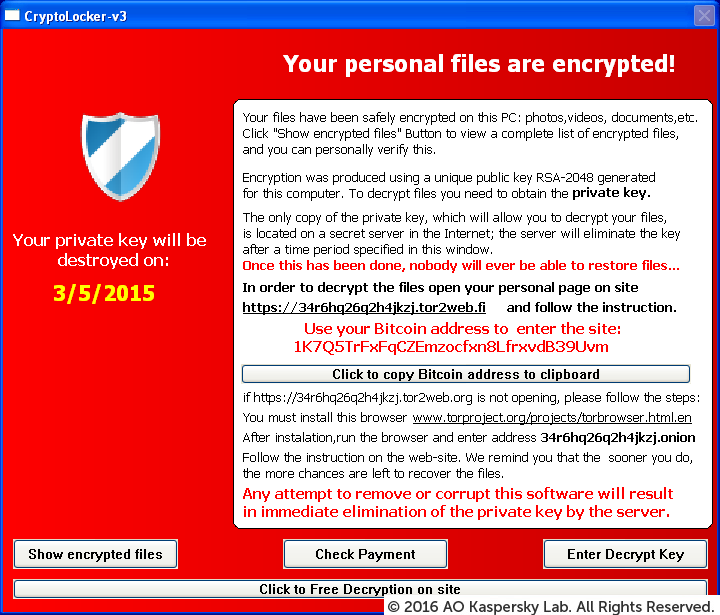
Types of Malicious Code (Ransomware)
Based on the impact on the target system and its characteristics.
Encryption Ransomware
Encrypts files and folders. Original files are deleted after encryption. A lock screen is typically displayed.
Lock Screen Ransomware
Locks the screen of the affected system and displays a payment request. It usually does not encrypt files or folders.
Master Boot Record (MBR) Ransomware
This type of ransomware modifies the MBR (Master Boot Record) of the system to interrupt the system startup.
Mobile Ransomware
Mainly affects the Android operating system. Infection usually originates from app downloads from unofficial Android markets.
Information on Ransomware
How Do Ransomware Attacks Work?
A ransomware attack is typically launched through an email attachment, which can be an executable file, a document, or an image. Once the attachment is opened, the malware spreads throughout the user’s system. Cybercriminals can also hide malware on websites, infecting the devices of visitors without their knowledge.
The infection is not immediately apparent to the user. The malware operates quietly in the background until it deploys a data-blocking mechanism. Then, a dialog box appears, notifying the user that their data has been locked and a ransom is required to unlock it. By this point, it’s often too late to save the data through security measures.
L’infezione non è evidente immediatamente per l’utente. Il malware opera silenziosamente in background fino a quando non viene attivato un sistema o un meccanismo di blocco dei dati. Successivamente appare una finestra di dialogo che informa l’utente che i dati sono stati bloccati e richiede un riscatto per sbloccarli. A quel punto è già troppo tardi per salvare i dati tramite misure di sicurezza.
Who Are the Victims of Ransomware?
Any user or business can fall victim to ransomware. Cybercriminals are generally not selective, often aiming to infect as many users as possible to maximize profit.
Are Ransomware Attacks on Businesses Increasing?
Yes, because cybercriminals know that organizations are more likely to pay, given that the affected data is often more sensitive and essential to business continuity. Additionally, it may sometimes be more costly to restore data from backups than to pay the ransom.
Is It Possible to Decrypt Files Encrypted by Ransomware?
In some cases, yes. This is possible in the following situations:
- The malware authors made implementation errors, allowing the encryption to be broken, as with the well-known ransomware Petya and CryptXXX.
- Keys or a master key are leaked, as in the case of TeslaCrypt.
- Authorities seize servers with keys and share them with the cybersecurity community, such as in the case of CoinVault.
Paying ransom is generally not recommended, but in cases involving large companies, it may be the only solution when no backups exist and each lost business hour translates into substantial financial loss.
In such cases, it’s recommended to use ransomware negotiation services like those provided by DarkData, which meticulously analyze adversaries to ensure payments lead to data recovery.
Should I Pay the Ransom if Infected?
Paying the ransom is not recommended without consulting an expert company, mainly because there’s no guarantee that the problem will be resolved. For example, there may be errors in the malware that prevent data recovery, even with the correct key.
In the event of a ransomware issue, multiple solutions may be available. Contact DarkData, and we’ll advise you.

